Difference between revisions of "CNM MediaWiki IAM"
| (17 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | [[CNM MediaWiki IAM]] | + | [[CNM MediaWiki IAM]] is the system that empowers [[identity and access management]] ([[identity and access management|IAM]]) of [[Educaship MediaWiki]] (hereinafter, ''Soft''). Within [[Opplet]], user credentials are stored at [[Educaship LDAP]]. |
| − | + | ||
| − | + | ||
| − | + | ==Issue build-up== | |
| − | + | For a few years, the stable version of the ''Soft'' has not been updated due to new versions' conflict with [[Educaship LDAP]]. Currently, the ''Soft'' uses an outdated, [[Special:Version|1.26.4 version]] of [[MediaWiki]], because the extension used to connect to its [[OpenLDAP]] does not support newer versions. At some period of time, [[CNM Technology Board]] considered three options: (1) to find or create a new extension, (2) to find another way to connect without using the extension, or (3) keep things as they are. | |
| − | + | ||
| + | At that time, the ''Board'' decided to keep things as they were since the current architecture was temporary. The ''Board'' believed that when a new private cloud based on [[OpenStack]] would be launched in the fourth phase of [[CNM Cloud Project]], its [[Keystone]] solution would be used for [[authentication]]s and [[authorization]]s. Plus, the ''Soft'' never contained any private information; all of its users' data was stored in [[Opplet.net]]. | ||
| + | |||
| + | Later, the ''Board'' also considered migration to the [[WSO2 IS]]-based integration and wasn't sure whether LDAP would remain necessary. | ||
| + | |||
| + | ==Current issue== | ||
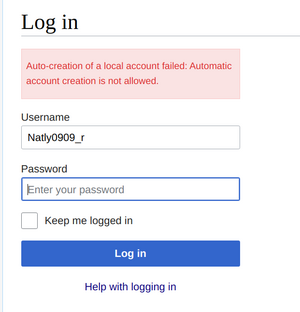
| + | Some when in early 2023, the even historic LDAP integration stopped functioning properly, possibly, because of outdated [[PHP]]-support. Here is a screenshot of the current issue: [[File:error_wiki.png|thumb|right]]<blockquote> | ||
<pre style="color: green"> | <pre style="color: green"> | ||
Symfony\Component\Ldap\Entry Object ( [dn:Symfony\Component\Ldap\Entry:private] => cn=natly0909_rou=applet,dc=career prize,dc=com | Symfony\Component\Ldap\Entry Object ( [dn:Symfony\Component\Ldap\Entry:private] => cn=natly0909_rou=applet,dc=career prize,dc=com | ||
| Line 11: | Line 17: | ||
</pre> | </pre> | ||
</blockquote> | </blockquote> | ||
| − | |||
| − | + | ==First attempt to resolve== | |
| + | While looking for any urgent solution that would allow for smooth work with the [[OpenLDAP]]-powered [[Educaship LDAP]], the team posted a job at [[Upwork]] in May of 2023. An expert coded as "LDAP-EC" was hired and provided with full access to the [[virtual machine]] with MediaWiki 1.39.3, PHP 8.1.2-1ubuntu2.11 (apache2handler), and MariaDB 10.7.8-MariaDB-1:10.7.8+maria~ubu2204 on which ''Soft's'' instance is installed as experiential environment and looked for complete documentation on what have been done. | ||
| + | |||
| + | ===Before awarding=== | ||
| + | LDAP-EC reported, | ||
| + | * Thanks for the invite, I'm an experienced Linux systems engineer with great LDAP skills, and I can help you set up an LDAP provider, a backup server, all client servers, and applications (APIs). I can secure it through TLS. | ||
| + | * I have read through the issue and identified some problems on it. For a start this is wrong: <code>cn=natly0909_rou=applet,dc=career prize,dc=com</code> | ||
| + | * I will need 4 hours to understand the hierarchy structure of your organization and the LDAP connection setup. | ||
| + | |||
| + | ===After awarding=== | ||
| + | LDAP-EC reported, | ||
| + | *Now, | ||
| + | *# PluggableAuth extension not installed | ||
| + | *# Older plugin used, need LDAPAuthentication2 | ||
| + | *# Wrong config of plugin | ||
| + | *# What is the LDAP bind address and password? | ||
| + | *# LDAP setup is ok although not secured with TLS | ||
| + | * Plan of action: | ||
| + | *# Install and configure the LDAPProvider plugin | ||
| + | *# Install and configure the PluggableAuth plugin | ||
| + | *# Install and configure the LDAPAuthentication2 plugin | ||
| + | *# Install some other LDAP package dependencies | ||
| + | *# Test connections using CLI | ||
| + | *# Test on web | ||
| + | * All the configurations are ok, it's just the PluggableAuth extension which needs some extra configs for the webUI login to work | ||
| + | |||
| + | ===Postponing=== | ||
| + | LDAP-EC reported, | ||
| + | *Finally, | ||
| + | *# I actually completed the setup before finding out that the PlugableAuth plugin version has some known issues with the new version of MediaWiki. The connection and authentication by the LDAP server is successful on the backend, but the plugin needs some more work for it to be functional on the webpage. | ||
| + | *# I can try to fix it, I don't know exactly how long it can take me. The reason for this is not that I don't know how to set it up, it's due to lack of maintenance from the plugin provider. So I find myself trying to fix and maintain a php code for which I wasn't hired for. It will be better to wait on the updated plugin than to waist money or effort on it and have no results. | ||
| + | *# As I said earlier, the connection from wiki to ldap is successful, but the plugin is not processing rightly the credentials passed on the web interface. | ||
| + | |||
| + | ==See also== | ||
| + | * https://www.mediawiki.org/wiki/Extension:LDAPProvider | ||
| + | * https://www.mediawiki.org/wiki/Manual:Active_Directory_Integration | ||
| + | * https://www.mediawiki.org/wiki/Manual_talk:Active_Directory_Integration | ||
Latest revision as of 23:22, 14 April 2024
CNM MediaWiki IAM is the system that empowers identity and access management (IAM) of Educaship MediaWiki (hereinafter, Soft). Within Opplet, user credentials are stored at Educaship LDAP.
Contents
Issue build-up
For a few years, the stable version of the Soft has not been updated due to new versions' conflict with Educaship LDAP. Currently, the Soft uses an outdated, 1.26.4 version of MediaWiki, because the extension used to connect to its OpenLDAP does not support newer versions. At some period of time, CNM Technology Board considered three options: (1) to find or create a new extension, (2) to find another way to connect without using the extension, or (3) keep things as they are.
At that time, the Board decided to keep things as they were since the current architecture was temporary. The Board believed that when a new private cloud based on OpenStack would be launched in the fourth phase of CNM Cloud Project, its Keystone solution would be used for authentications and authorizations. Plus, the Soft never contained any private information; all of its users' data was stored in Opplet.net.
Later, the Board also considered migration to the WSO2 IS-based integration and wasn't sure whether LDAP would remain necessary.
Current issue
Some when in early 2023, the even historic LDAP integration stopped functioning properly, possibly, because of outdated PHP-support. Here is a screenshot of the current issue:
Symfony\Component\Ldap\Entry Object ( [dn:Symfony\Component\Ldap\Entry:private] => cn=natly0909_rou=applet,dc=career prize,dc=com [attributes:Symfony\Component\Ldap\Entry:private] => Array ( [uid] => Array ([0] => natly0909_r ) [0] => Array ( [0] => Zina ) [I] => Array ( [0] => Sinih ) [gecos] => Array [0] na...@gmail.com )))
First attempt to resolve
While looking for any urgent solution that would allow for smooth work with the OpenLDAP-powered Educaship LDAP, the team posted a job at Upwork in May of 2023. An expert coded as "LDAP-EC" was hired and provided with full access to the virtual machine with MediaWiki 1.39.3, PHP 8.1.2-1ubuntu2.11 (apache2handler), and MariaDB 10.7.8-MariaDB-1:10.7.8+maria~ubu2204 on which Soft's instance is installed as experiential environment and looked for complete documentation on what have been done.
Before awarding
LDAP-EC reported,
- Thanks for the invite, I'm an experienced Linux systems engineer with great LDAP skills, and I can help you set up an LDAP provider, a backup server, all client servers, and applications (APIs). I can secure it through TLS.
- I have read through the issue and identified some problems on it. For a start this is wrong:
cn=natly0909_rou=applet,dc=career prize,dc=com - I will need 4 hours to understand the hierarchy structure of your organization and the LDAP connection setup.
After awarding
LDAP-EC reported,
- Now,
- PluggableAuth extension not installed
- Older plugin used, need LDAPAuthentication2
- Wrong config of plugin
- What is the LDAP bind address and password?
- LDAP setup is ok although not secured with TLS
- Plan of action:
- Install and configure the LDAPProvider plugin
- Install and configure the PluggableAuth plugin
- Install and configure the LDAPAuthentication2 plugin
- Install some other LDAP package dependencies
- Test connections using CLI
- Test on web
- All the configurations are ok, it's just the PluggableAuth extension which needs some extra configs for the webUI login to work
Postponing
LDAP-EC reported,
- Finally,
- I actually completed the setup before finding out that the PlugableAuth plugin version has some known issues with the new version of MediaWiki. The connection and authentication by the LDAP server is successful on the backend, but the plugin needs some more work for it to be functional on the webpage.
- I can try to fix it, I don't know exactly how long it can take me. The reason for this is not that I don't know how to set it up, it's due to lack of maintenance from the plugin provider. So I find myself trying to fix and maintain a php code for which I wasn't hired for. It will be better to wait on the updated plugin than to waist money or effort on it and have no results.
- As I said earlier, the connection from wiki to ldap is successful, but the plugin is not processing rightly the credentials passed on the web interface.