Difference between revisions of "System-User Roles"
(→Key terms' outline) |
(→Lectio 3 presentation) |
||
| Line 23: | Line 23: | ||
:Some permissions such as appointing other administrators and alternating the algorithms must be done manually. In [[cyber-security]], those operations are called [[identity and access management]] ([[identity and access management|IAM]]). | :Some permissions such as appointing other administrators and alternating the algorithms must be done manually. In [[cyber-security]], those operations are called [[identity and access management]] ([[identity and access management|IAM]]). | ||
| + | |||
| + | The successor [[lectio]] is [[CNM Cyber SSO]]. | ||
===Lectio 3 quiz questions=== | ===Lectio 3 quiz questions=== | ||
Revision as of 14:29, 21 April 2020
System-User Roles (hereinafter, the Lectio) is the lesson part of the CNM Cabin Essentials lesson that introduces its participants to CNM Cabin. This lesson belongs to the CNM Cyber for Experience session of the CNM Cyber Welcome Course.
Contents
Content
The predecessor lectio is Managers of User Data.
Key terms
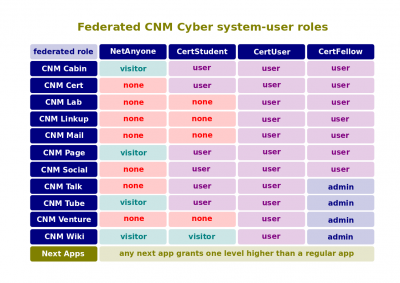
|3||System-user role, NetAnyone, CertStudent, CertUser, CertFellow
- System-user role. The set of capacities often called permissions that a system grants to any user who belongs to a particular role.
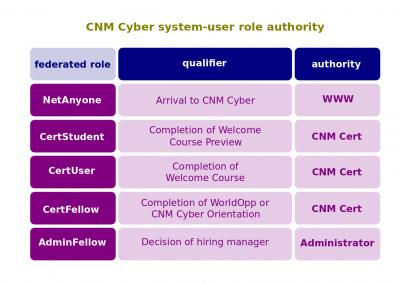
- NetAnyone. The system-user role for an end-user of the World Wide Web whom CNM Cyber hasn't identified yet.
- CertStudent. The system-user role that CNM Cyber grants upon completion of the CNM Cyber Welcome Course Preview.
- CertUser. The system-user role that CNM Cyber grants to any graduate from the CNM Cyber Orientation.
- CertFellow. The system-user role that CNM Cyber grants to any graduate from CNM Cyber Placement.
System-User Names
System-User Names is the third lectio out of six ones that make up the Lesson.
Lectio 3 presentation
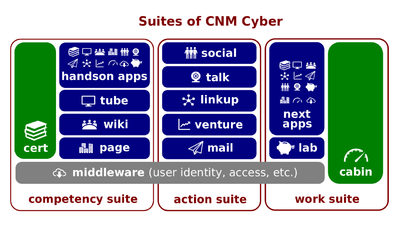
- The bulk of permissions are granted automatically. To accomplish that task, CNM Cabin assigns every user with his or her system-user role. For instance, any user of the World Wide Web has NetAnyone's rights at CNM Cyber. He or she can view pages of CNM Page, CNM Tube, and CNM Wiki, but cannot edit anything. CertStudents are enrolled into this very welcome course, as well as can post comments on CNM Page and CNM Tube. CertUser's can join communities at CNM Social, and so on.
- Some permissions such as appointing other administrators and alternating the algorithms must be done manually. In cyber-security, those operations are called identity and access management (IAM).
The successor lectio is CNM Cyber SSO.